Methods of Internet Censorship
Article by Jonathan SticklesConfiscation & Arrest
The most traditional and straightforward method of censorship in all media is to arrest violators and confiscate censored materials. This technique extends to Internet censorship as well. However, unlike most media, the Internet provides an international forum for people to express their views and share data, often anonymously.
Users can avoid this form of censorship by staying anonymous, hosting their sites in other countries, or even being in another country themselves. Even if the computers hosting the information are able to be confiscated, maintaining offsite backups and contingency plans may allow a site to come back online quickly, despite direct intervention.
Denial of Service Attacks
If the computer cannot be physically attacked, it may still be possible to crash it or make it unresponsive by sending an enormous amount of requests to the server, more than its processor or bandwidth can handle. This technique usually takes the form of a DDoS, or Distributed Denial of Service attack, in which hundreds or thousands of computers all try to simultaneously and repeatedly communicate with the targeted computer. Due to the amount of computer resources needed to carry out this kind of attack, these attacks are temporary, sometimes merely symbolic.
Although Denial of Service attacks do not permanently disable a site, they can still be economically damaging, as well as frustrating for users who use the web site or service and find their access cut off. Users can�t bypass the attack, but the server owner or ISP may be able to successfully filter out the offending requests before the bottleneck to effectively defeat the attack while it is still ongoing.
Content Filtering
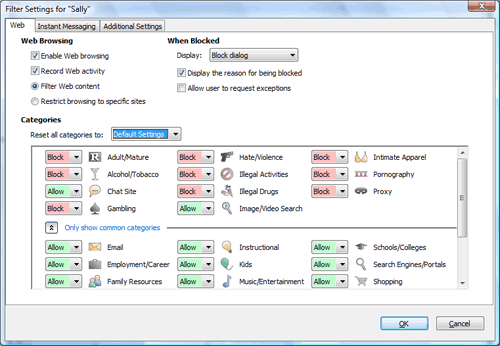
Net Nanny is an example of commercial content filtering software marketed to concerned parents.
Due to the heavily international nature of the Internet, and the millions and millions of users online, other methods beyond just directly attacking an offending computer are necessary for most censorship efforts to be effective. One approach is to filter content by scanning the data coming in, and determine if it is appropriate. This technique is sometimes by web sites complying with government mandates to selectively filter some expression as a condition of allowing the rest of the site to stay unfiltered. More broad automated analysis of web page content is generally not seen outside of commercial software designed to make the web safer for children, perhaps due to the technical overhead needed to intercept and filter all communications using this method. A simpler version that has been implemented by some countries involves scanning URLs for suspicious keywords, and blocking them if they appear to be inappropriate.
Due to the imprecision in this technology, it necessarily filters out many web sites that are not intended to be censored, and can miss some content that would have been censored. Depending on where the data is sampled, this can sometimes be bypassed by encrypting the communications so that the content filter cannot recognize any banned words or patterns.
Simple Monitoring
Even if filtering all content is not viable, the mere knowledge that the government is overtly monitoring users can be used to discourage forbidden speech, as well as to make it easier to act against those who don�t get the message. This monitoring can take several forms, from the comparatively benign (Chinese news sites requiring users to register with their real names before commenting) to extremely intrusive (Cuban Internet cafes that snoop all email). (The Guardian: 1, 2) This is also a time-honored tactic by parents seeking to keep their children in good behavior.
IP Filtering
A more narrow and pointed technique is to use a firewall to filter out specific IP addresses, which are the unique identifiers computers use to identify each other and send messages on the Internet. By intercepting messages and discarding ones sent to or from a list of blacklisted IPs, entire sections of the Internet can be hidden from view. This technique requires maintaining a list of prohibited sites, and intercepting communications at key points. It has been successfully used in many countries, including Australia and the United Kingdom.
Although effective for most users, IP filtering can be easily bypassed by not contacting the blocked computers directly. Sending requests to an unblocked proxy server or forming a VPN (Virtual Private Network) with a computer on the other side of the firewall, and having the other computer talk to the blocked sites on your behalf, will allow the same data to be passed through the filter without triggering the IP block. There are many thousands of free anonymous proxy servers distributed throughout the world, and easy support for their use is built into several major browsers, including Firefox and Chrome.
DNS Delisting
Another mechanism for preventing people from accessing specific web sites is to delist the site�s domain name from DNS (Domain Name Service) registries. People use human-readable URLs (such as www.google.com) to specify web pages they want to access, but these URLs don�t, in themselves, identify a computer. They have to be sent to a DNS server to be looked up on a table of known domain names and their associated IP addresses. The IP address then points to a computer. By delisting some URLs from the DNS registries, computers can remain online and unfiltered, but still be difficult to access, since typing their URL into a browser will return an error instead of reaching the web site. DNS delisting will also affect links between web sites, since links typically identify other web sites using URLs rather than IP addresses. A similar but distinct method is to intercept and scan all DNS requests before they arrive at the registry, and block requests for banned URLs.
DNS delisting can be bypassed if the user already knows the correct IP address, or is able to contact a different DNS server that hasn�t delisted the site. If you know the correct IP address, you can either modify your computer�s HOSTS file, which locally associates IP addresses with URLs and bypasses the DNS registry, or you can just type the IP address into the browser directly. Because the delisted web site is still connected to the Internet, only hidden, your direct request for their IP will go through as long as the IP itself is not filtered, and the web site will display.
Portal Delisting
With Portal Delisting, an effort is made to prevent users from finding the URL in the first place, by removing all mention of the web site from major web portals, such as Google. Most major web portals cooperate with this with when it is imposed by law, but only on a country-by-country basis. For example, Google Germany delists neo-Nazi websites, but Google�s English site does not. Google caused a major stir last year when it redirected all traffic from its Chinese portal to an unfiltered search in Hong Kong, in retaliation for suspected hacking. China responded by adding all Google services to their IP blacklist, thereby forcing people to use web portals that were complying with domestic law. (Net Security)
Portal delisting can be bypassed by finding another site that links to the censored content, or typing the URL in directly. Because portals delist on a country-by-country basis, it can also be bypassed by visiting another version of the portal. For example, even when Google was allowed in China and was cooperating with government censorship, a savvy user in China could use a proxy server to bypass the block on other versions of Google, visit Google�s unfiltered English portal, and search as normal using Chinese search text.
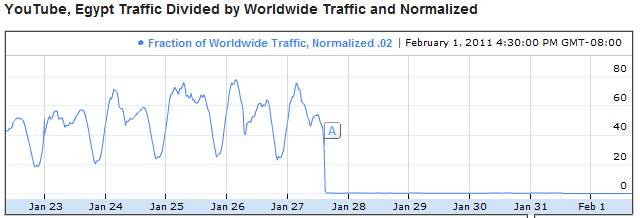
Millions of web browsers cried out in terror and were suddenly silenced...
Kill Switch
The vast size of the Internet combined with the existence of anonymous proxy servers and many services based in other countries makes online activities impossible to control completely. One approach is to seal an entire country off from the net. Some countries, like North Korea, restrict access to the point that few people are able to get online at all. (Korea Times) Others allow extensive access, but maintain emergency plans for shutting down all access to the Internet.
This more dramatic tactic was unheard of before this year, which saw Egypt, Libya, and Syria all separately cut off almost all network traffic into and out of their respective countries, by shutting down connections through major ISPs. All three restored Internet access within a week. Cutting the Internet off completely has yet to be successful at suppressing domestic unrest, as Egypt�s government fell shortly afterward, Libya is now embroiled in civil war, and Syria continues to see reports of spiraling violence between protesters and police. (Reuters)
Sources and Additional Reading
OpenNet - About Filtering
Communication Crisis - The Sound of Silence: Censorship on the Internet
